Figure 1: An example of the trace headers on an e-mail
message, which in this case has passed many servers on its route from
the original sender to the final recipient. Headers are added at the
top, so the last header in the list represents the original submission
of this message.
To gain higher protection of anonymity, a clever impostor
can use various techniques to make identification more difficult. Examples
of such techniques are:
- IP numbers, trace lists and other identification can be falsified. Since this information is often created in servers, it is easier to falsify them if you have control of one or more servers.
- Communication is done in several steps. The impostor first connects to computer A, then from this computer to computer B, then from this to computer C, etc. To find the real person, all the steps must be followed backward. The trace needs transaction logs, and such logs are not always produced automatically. Logging may have to be switched on. So by co-operating with the owner of computer C, it is possible to switch on logging so that the next time the impostor appears, he is traced back to computer B. In the next step, the owner of computer B is asked to help trace the impostor further. Thus, through a tedious process, including the co-operation of all the used computers in the chain, the real person can be found. A famous example is described in the book [Stoll 1989], which describes the tracing of a hacker which used a series of servers, without permission, to conceal the route from the user to the final anonymous activity.
Anonymity servers
Since anonymity has positive uses (see above) there are
people who run anonymity servers. An anonymity server receives messages,
and resends them under another identity. There are two types of anonymity
servers:
- Full anonymity servers, where no identifying information is forwarded.
- Pseudonymous servers, where the message is forwarded under a pseudonym. The server stores the real name behind a pseudonym, and can receive replies sent to the pseudonym, and transmit them back to the originator.
Anonymity servers often use encryption of the communication,
especially of the communication between the real user and the server,
to increase the security against wiretapping.
There are companies which market anonymity servers and
there is a research area on improving the techniques of such software
[McCullagh 2001].
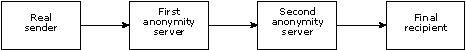
People who want to achieve high security against being
revealed, often use several anonymity servers in sequence. To trace
them, each of the servers must assist or be penetrated (see Figure
2 ). If the servers are placed in different countries, tracing them
becomes even more difficult.
Figure 2: Steps to hide the real identity through
several servers
A user might send a message to the first anonymity server,
instructing it to send the message to the second anonymity server, which
is instructed to send the message to the final recipient.
An example: Anon.penet.fi
Anon.penet.fri was a pseudonymity server started by Johan
Helsingius in Finland in 1992. It was very popular by people in other
countries, since they thought that relaying messages through an anonymity
server in Finland would reduce the risk of their real identity being
divulged. At its peak, it had 500 000 registered users and transferred
10 000 messages per day.
There was a lot of controversy regarding this server.
Example 1: Some people claimed that the server was used
to distribute child pornography. This was both true and false. The server
had been used to communicate between providers and consumers about child
pornography. The actual pictures, however, had not been transmitted
through the server, even though they had been wrongly marked-up as coming
from the server. The server, in fact, had such a low limit on the maximum
size of messages, that only very small pictures (less than 48 kbyte)
could be sent through it.
Example 2: The server was used by a former member of the
American quasi-religious organization “Scientology Church”
to distribute secret documents from this organization to the public.
The organization asked American police for help, claiming that the messages
infringed on their copyright. The American police contacted the Finnish
police in the spring of 1996, and the Finnish police forced Helsingius
to tell them the real name behind these messages. The way in which the
police in the U.S.A. and Finland treated this issue has been criticized
afterwards.
As a result of these and other cases, Helsingius stopped
his server in August 1996.
The Scientology Church has also attempted to stop newsgroups
discussing the Church on the Internet using various technical means
such as falsified CANCEL commands.
Statistics on the Use of Anonymity
Mikael Berglund made a study on how anonymity was used. His study was based on scanning all publicly available newsgroups in a Swedish Usenet News server, which downloaded almost everything written in Usenet News internationally in September 1995. He randomly selected a number of messages, which were pseudonymous and were shown as coming from anon.penet.fi (they may not always in reality have passed through anon.penet.fi), and classified the topic of these messages. His results were as follows: